Leverage CVE-2024-3661 TunnelVision to Effectively Disable VPN for iPhone Users
DHCP can add routes to a client’s routing table via the classless static route option 121. This blog post discuses how to take advantage of that fact to render VPN on iPhones useless.

This is Based on a research done by the Leviathan Security Group https://www.leviathansecurity.com/blog/tunnelvision
For an introduction and details on this security concern, please refer to the linked research above.
As outlined in the original research, most operating systems, including iOS, are vulnerable to the TunnelVision bug.
To exploit this flaw, a DHCP server capable of serving DHCP option 121 (Classless Static Route Option) is required.
Upon testing on an iPhone using a DHCP server that serves the routes 0.0.0.0/1 and 128.0.0.0/1, and subsequently connecting the iPhone to a privacy VPN, internet connectivity appears to be lost.
After numerous attempts, it was discovered that iOS detects any route that starts with 0.0.0.0 and treats it in a special way, resulting in a conflict when a VPN service attempts to add a default route to the iOS routing table.
Therefore, to render the VPN switch for iPhone users useless (and misleading), it is necessary to avoid using 0.0.0.0 and instead have a DHCP server serve the following routes:
- 1.0.0.0/8 VIA ROUTER
- 2.0.0.0/7 VIA ROUTER
- 4.0.0.0/6 VIA ROUTER
- 8.0.0.0/5 VIA ROUTER
- 16.0.0.0/4 VIA ROUTER
- 32.0.0.0/3 VIA ROUTER
- 64.0.0.0/2 VIA ROUTER
- 128.0.0.0/1 VIA ROUTER
In my case, I was using pfSense's DHCP server, and I needed to pass the routes as a HEX string. This can be achieved using the following HEX:
08:01:c0:a8:b4:01:07:02:c0:a8:b4:01:06:04:c0:a8:b4:01:05:08:c0:a8:b4:01:04:10:c0:a8:b4:01:03:20:c0:a8:b4:01:02:40:c0:a8:b4:01:01:80:c0:a8:b4:01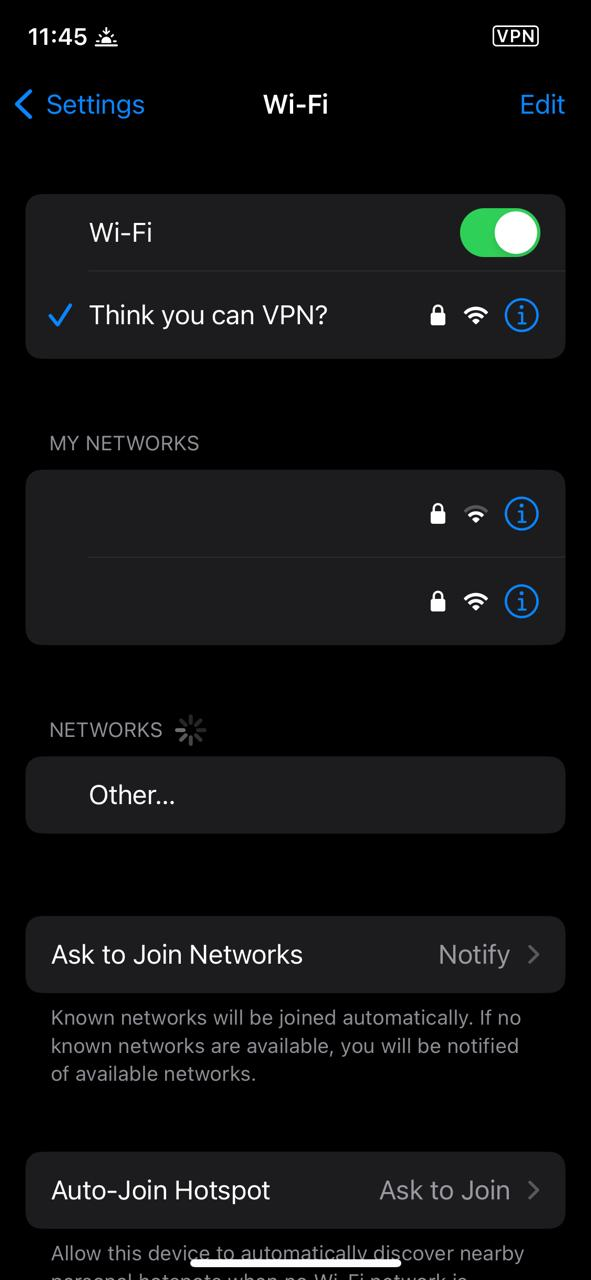
Mitigation
Switch to Android :)
There is really not much you can do about this flaw other than being cautious when connecting to untrusted WiFi networks and do the following when connecting to a VPN:
- Check routes using HE Tools app.
- Traceroute after connecting to a VPN to check packets path.
- If the goal of the VPN is to change the public IP address, then check IP before and after connceting to the VPN.
